はじめに
Fortigate では、IPsec で VPN を構築しつつ、NAT によるオリジナル IP の送信元/宛先同時変換が可能です。基本的に、送信元 NAT は Pool を使用し、宛先 NAT は、VIP を使用します。
以下、想定環境と設定例になります。
以下、想定環境と設定例になります。
想定環境
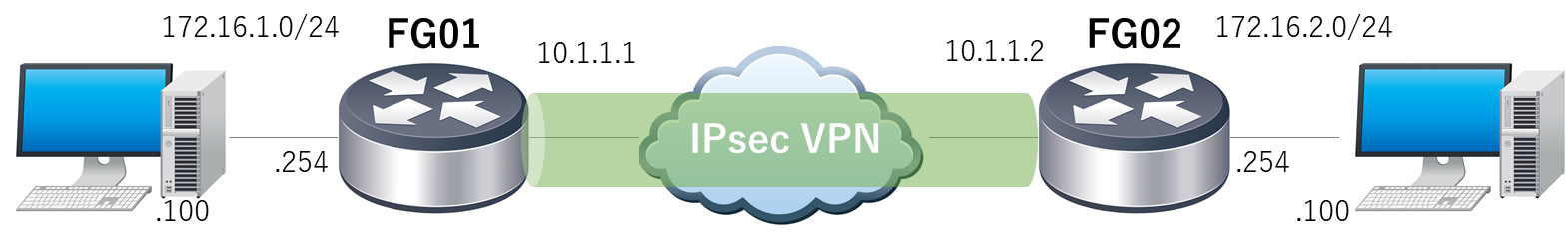
FortiGate IPsec VPN(with NAT)設定例
LAN の設定
config system interface
edit "port3"
set vdom "root"
set ip 172.16.1.254 255.255.255.0
set allowaccess ping
set type physical
set snmp-index 3
set macaddr 00:0c:29:87:90:99
endconfig system interface
edit "port3"
set vdom "root"
set ip 172.16.2.254 255.255.255.0
set allowaccess ping
set type physical
set snmp-index 3
set macaddr 00:0c:29:5c:5b:53
endWAN の設定
config system interface
edit "port2"
set vdom "root"
set ip 10.1.1.1 255.255.255.0
set allowaccess ping
set type physical
set snmp-index 2
set macaddr 00:0c:29:87:90:8f
endconfig system interface
edit "port2"
set vdom "root"
set ip 10.1.1.2 255.255.255.0
set allowaccess ping
set type physical
set snmp-index 2
set macaddr 00:0c:29:5c:5b:49
endIKE フェーズ 1 の設定
config vpn ipsec phase1-interface
edit "Site-to-Site"
set interface "port2"
set remote-gw 10.1.1.2
set psksecret ENC
endconfig vpn ipsec phase1-interface
edit "Site-to-Site"
set interface "port2"
set remote-gw 10.1.1.1
set psksecret ENC
endIKE フェーズ 2 の設定
config vpn ipsec phase2-interface
edit "Site-to-Site"
set phase1name "Site-to-Site"
endconfig vpn ipsec phase2-interface
edit "Site-to-Site"
set phase1name "Site-to-Site"
endスタティックルートの設定
config router static
edit 1
set dst 10.1.1.2 255.255.255.255
set device "Site-to-Site"
next
edit 2
set dst 10.1.1.102 255.255.255.255
set device "Site-to-Site"
endconfig router static
edit 3
set dst 10.1.1.1 255.255.255.255
set device "Site-to-Site"
next
edit 2
set dst 10.1.1.101 255.255.255.255
set device "Site-to-Site"
endIP Pool(送信元 NAT)の設定
config firewall ippool
edit "SNAT_Pool"
set startip 10.1.1.1
set endip 10.1.1.1
endconfig firewall ippool
edit "SNAT_Pool"
set startip 10.1.1.2
set endip 10.1.1.2
endVIP(宛先 NAT)の設定
config firewall vip
edit "FG01-to-FG02_VIP01"
set extip 10.16.2.100
set extintf "port3"
set mappedip "10.1.1.102"
next
edit "FG02-to-FG01_VIP01"
set extip 10.1.1.101
set extintf "Site-to-Site"
set mappedip "172.16.1.100"
endconfig firewall vip
edit "FG02-to-FG01_VIP01"
set extip 10.16.1.100
set extintf "port3"
set mappedip "10.1.1.101"
next
edit "FG01-to-FG02_VIP01"
set extip 10.1.1.102
set extintf "Site-to-Site"
set mappedip "172.16.2.100"
endPolicy の設定
config firewall policy
edit 1
set name "VPN_FG01-to-FG02"
set srcintf "port3"
set dstintf "Site-to-Site"
set srcaddr "all"
set dstaddr "FG01-to-FG02_VIP01" "FG01-to-FG02_VIP02"
set action accept
set schedule "always"
set service "ALL"
set nat enable
set ippool enable
set poolname "SNAT_Pool"
next
edit 2
set name "VPN_FG02-to-FG01"
set srcintf "Site-to-Site"
set dstintf "port3"
set srcaddr "all"
set dstaddr "FG02-to-FG01_VIP01" "FG02-to-FG01_VIP02"
set action accept
set schedule "always"
set service "ALL"
endconfig firewall policy
edit 1
set name "VPN_FG02-to-FG01"
set srcintf "port3"
set dstintf "Site-to-Site"
set srcaddr "all"
set dstaddr "FG02-to-FG01_VIP01" "FG02-to-FG01_VIP02"
set action accept
set schedule "always"
set service "ALL"
set nat enable
set ippool enable
set poolname "SNAT_Pool"
next
edit 2
set name "VPN_FG01-to-FG02"
set srcintf "Site-to-Site"
set dstintf "port3"
set srcaddr "all"
set dstaddr "FG01-to-FG02_VIP01" "FG01-to-FG02_VIP02"
set action accept
set schedule "always"
set service "ALL"
end確認コマンド
NAT 状況の確認
PC01(172.16.1.100)から PC02(10.16.2.100:VIP)へ Ping を実行時、172.16.1.100 は、10.1.1.1 に送信元 NAT され、10.16.2.100 は、10.1.1.102 に宛先 NAT されています。
diagnose debug enable
diagnose debug flow trace start 20
id=20085 trace_id=2336 func=print_pkt_detail line=4696 msg="vd-root received a packet(proto=1, 172.16.1.100:22308->10.16.2.100:8) from port3. code=8, type=0, id=22308, seq=9."
id=20085 trace_id=2336 func=resolve_ip_tuple_fast line=4760 msg="Find an existing session, id-0002f029, original direction"
id=20085 trace_id=2336 func=ipv4_fast_cb line=53 msg="enter fast path"
id=20085 trace_id=2336 func=ip_session_run_all_tuple line=5825 msg="DNAT 10.16.2.100:8->10.1.1.102:22308"
id=20085 trace_id=2336 func=ip_session_run_all_tuple line=5813 msg="SNAT 172.16.1.100->10.1.1.1:62464"
id=20085 trace_id=2336 func=ipsecdev_hard_start_xmit line=157 msg="enter IPsec interface-Site-to-Site"
id=20085 trace_id=2336 func=esp_output4 line=846 msg="IPsec encrypt/auth"以上
[sitecard subtitle=関連記事 url=https://mytech-blog.com/fortigate-ipsec-vpn/ target=]
参考書籍
created by Rinker
¥3,080
(2026/01/31 13:03:02時点 楽天市場調べ-詳細)